16
A clear view of the question: “why doesn’t Belgium have a government yet?”
Posted in General on January 16th, 2011 by NicolasThis is a great video, I’d be more than happy to be the “francophone” that M. Janssens refers to as his marching buddy.

16
This is a great video, I’d be more than happy to be the “francophone” that M. Janssens refers to as his marching buddy.
3
Inside each of the wagons of the Toulouse’s metro, two network maps are displayed so you can easily spot the station names, order and BUS/Metro connections as you ride. However, since the opening of line “B” in June 2007, some BUS lines have been re-organized in order to cope with the “new and unpredictable” affluence that has been noticed at some stations. This lead to a change in the connections map.

29
I used to have a simple policy for my wifi network which would be “open” with no crypto whatsoever. I did this in order to allow for any visitor at home to be able to surf without having to share a secret with him. However, I soon realized that this was not good for the “privacy” of my data and turned to an OpenVPN-based solution in order to protect the traffic from my “known” hosts. This being done, in the absence of visitors, I would simply stop routing wireless traffic that was not VPN.
However, the advent of WPA and WPA-Enterprise made me believe that there was a simpler solution that would allow me to achieve the same thing but in a way that would also allow my visitors to benefit from some “privacy”. However, I still didn’t want to share a secret with them nor did I want to have them install anything on their machine.
Setting up WPA2 on my access point and coupling that with a Radius server was the solution I was looking for!
28
In order to setup an ssh tunnel between port 8080 on the local machine and port 80 on the SSH server, you can go and type:
ssh -L8080:localhost:80 machine.example.org -l yourUsernameAtMachineDOTexampleDOTorg
But if you follow the law of the least effort, you won’t want to type that in everytime you need to establish the tunnel, you would rather type:
ssh tunnelName
and have SSH do everything by itself for you! This can be acomplished by inserting the following lines in your ~/.ssh/config file.
Host tunnelName User yourUsernameAtMachineDOTexampleDOTorg Hostname machine.example.org GatewayPorts yes LocalForward 8080 localhost:80
Notice the GatewayPorts yes directive, this is optional for the tunnel to come up but allows you to use the tunnel from other machines than just the one that establishes it!
26
Since 2004, I’m a member of the Thawte Web of Trust. I’ve always been quite a security enthusiast, my first experiences were under DOS using the pgp executable to try and cypher some text that I would put on a diskette and have a friend read the next day…
Those days are long gone but, even though the advent of the Internet and modern cryptography, the principles still remain! In the beginning there are only two things, a Public and a Private cryptographic key. The public key is used for cyphering content and verifying signatures, the private key is used to sign and decipher content.
So if you want to send a message to a friend of yours, you have various options:
That’s a lot of key exchanges that could potentially lead to several attacks such as Eve trying to convince you that he’s got your friends’ public key when what he has is a fake. Eve, if she somehow catches the message you sent your friend will be able to decipher it.
Now, this is where certificates come into action, Trent which is trusted by both of you will “grosso modo” digitally sign your (name, email address and public key) tuple so it can not be tampered with. Of course, Trent needs to assert your identity before he signs your certificate, otherwise it makes no sense.
Thawte is just an instance of Trent, also known as a Certification Authority which delivers free personal certificates for email based on the concept of a Web of Trust (WoT)!
21
Have you ever wanted to show others where you went and what your itinerary was to get there? If you’re starting a photo book about your last trip around China or your latest safary through Africa, here is a tool that might come in handy.
This online tool by Karl L. Swartz generates a map of your trips
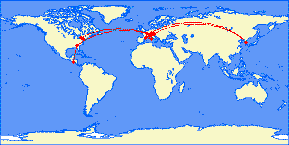
13
The race for storage space between Yahoo! and Google has already been discussed on many blogs lately. The decision by Yahoo! to offer unlimited storage space for your emails has been welcome by most! I personally still prefer Gmail which to my opinion has much more usability than Yahoo!. This is specially true when combined with Google Calendar (or Agenda) and other Google goodies such as Google Notepad, Google Stocks, Picasa etc…
There is however, something not so logical when it comes to space and Google….
10
While watching the french (TF1) TV news someday this week, I’ve discovered the existence of Spock! after a little google search, I also found this post on Mashable France about it.
These guy’s goal is to do some kind of wikipedia/linkedIn/hi5 hybrid that will not only contain information that someone enters into it but also information that is gathered automatically, much in the way search engines do. The preliminary results look very nice!
The fact that I had a LinkedIn profile alone was enough for them to find me and have me in there.
Read more »
7
For some of the latest projects I’m working on, it is required that I quite frequently access various machines that are located behing a corporate firewall, on a privately adressed subnet inside a company.
One option I had but got fed up with quite fast was :
outside$ ssh nicolas@gateway gateway$ ssh root@box1 box1# or ssh -t nicolas@gateway ssh root@box1
Once again, SSH came in handy and I found that everything was there for me to have that first hop and re-ssh done automatically. Just added the following to my ~/.ssh/config
Host gateway Hostname gateway.example.org User nicolas Host box1 Hostname 192.168.0.1 User root ProxyCommand ssh gateway nc -w 1 %h 22
This, coupled to ssh’s passwordless authentication made my day a lot easier ;)
6
Hellow, I’m trying to test this thing to see how nice it can become.. Long life to the bloggers and blogs all over the plannet… I hope I’ll ever find a use for this nice custom blog on my website.. If I don’t ever find any, don’t worry, be happy! C-Ya Nicolas